Atelier HLP - Photos d'enfance - Parcours Education Artistique et Culturelle (PEAC) - LYCEE THEOPHILE ROUSSEL

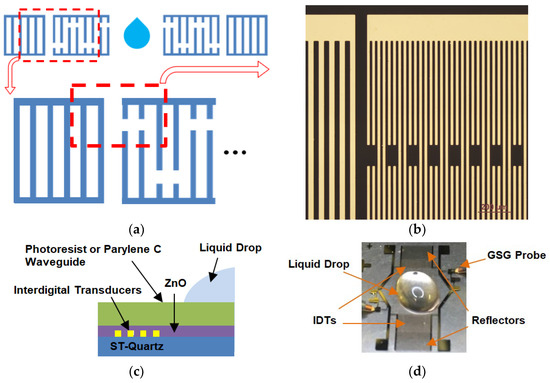
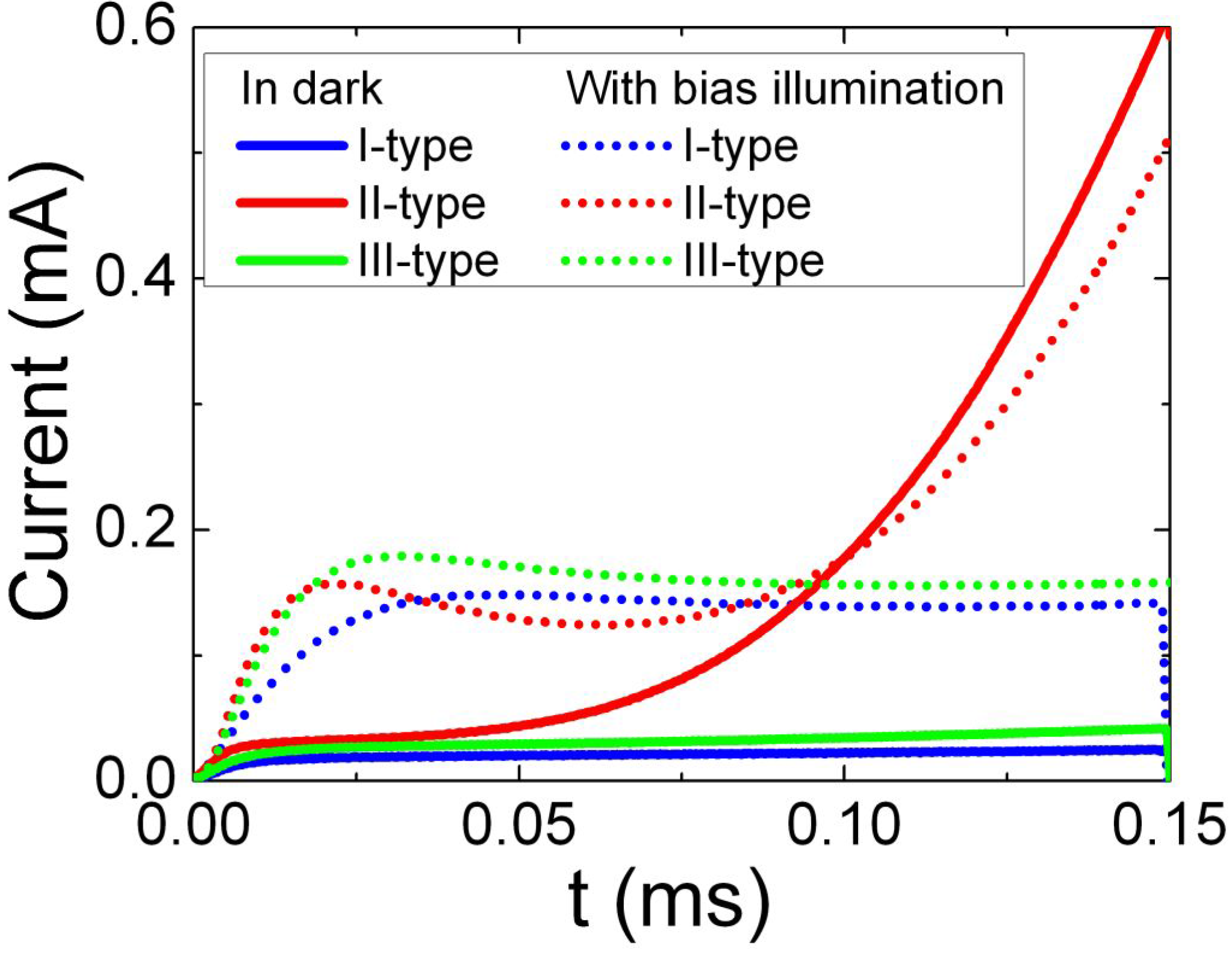
Contactless pre-bond TSV fault diagnosis using duty-cycle detectors and ring oscillators | Semantic Scholar

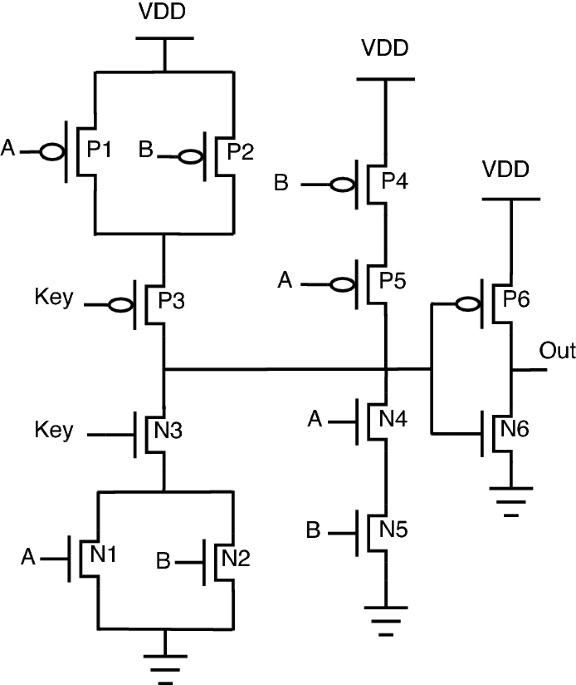
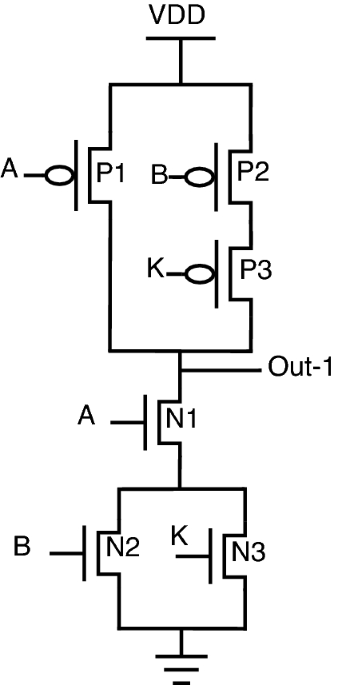
Hardware obfuscation of AES IP core using combinational hardware Trojan circuit for secure data transmission in IoT applications - Chhabra - 2022 - Concurrency and Computation: Practice and Experience - Wiley Online Library

PDF) Improving Datapath Testability by Modifying Controller Specification | Marie-lise Flottes - Academia.edu
TEST GENERATION FOR SYSTEM-ON-CHIP SECURITY VALIDATION By YANGDI LYU A DISSERTATION PRESENTED TO THE GRADUATE SCHOOL OF THE UNIV

Contactless pre-bond TSV fault diagnosis using duty-cycle detectors and ring oscillators | Semantic Scholar